Why traditional Windows application management is broken - and what modern IT teams must do instead
October 15th, 2025
5 min read
By Barry Angell

Windows application security is no longer just an IT concern—it’s a business-critical priority for enterprises and large organizations. Yet many still operate with outdated, manual processes that leave gaping holes in their application coverage. This leaves them struggling to keep up with the velocity of modern software deployment, increasing their potential risk exposure.
Why? The reason why so many organizations struggle is simple: the traditional approach to Windows application management is fundamentally broken. Most organizations still rely on 20-year-old processes and tools to get Windows applications packaged and ready for their IT environment. It simply is inadequate to meet today’s security and performance expectations. And to fix it, you will need to adopt a radically different mindset—one that embraces automation, redefines roles, and prioritizes speed without sacrificing control.
The risk from incomplete Windows application coverage
Large organizations and enterprises have to accept application security risk through vulnerabilities that exist in their IT environment. The two main issues are:
- Inability to update Windows applications quickly enough. This applies to both managed (packaged and/or distributed centrally) and unmanaged (those apps that are not updated through central operations) applications.
- Lack of visibility into the unmanaged Windows application landscape. IT teams often do not know these unmanaged applications even exist, and consequently don’t have a proper way to track them outside of security scans.
As a result, organizations often operate in a broken environment where 100% application coverage is unachievable. Critical and important security updates are delayed, creating unmitigated risks that can further stretch the IT team’s resources.
This is inefficient, slow, and dangerous.
The bottlenecks behind the breakdown
Why is it so hard to keep applications current and secure? Fundamentally, most application packaging teams are still following core processes that are 20+ years old, processes that take a lot of time and money to administer.
For Windows application owners, this application packaging process often involves extensive manual repackaging, long wait times, and redundant efforts across teams. It’s not uncommon for a single Windows application to take anywhere from two to 20 days to get through the packaging and testing cycle, depending on its complexity.
To add to the burden Windows application packaging teams face, the demand for new desktop-based applications and application updates are coming in at a faster cadence than ever before. For example, in the past 12 months (since Apr 1st 2024), Adobe Acrobat Reader has received 12 major updates, 10 optional updates and 5 critical security updates (27 in total). Even without this volume, teams are often already at capacity with current demand, and often face throughput issues which are exacerbated with the current cadence of update releases.
This additional volume drives up both cost and friction. In response, organizations typically fall into one of the following categories:
- Do nothing, which is what a lot of companies today have defaulted to, knowing full well they are accepting risks on an ongoing basis.
- Add more people to the Windows app packaging and testing team - increasing costs significantly, just to keep up, and not fixing the root cause.
- Invest in package catalogs, which will give a small percentage of pre-packaged Windows application coverage, but don’t fix the underlying capacity issues.
However, enterprises can adopt a modern approach and fix the root issues at hand, using automation tools such as Juriba App Readiness.
A modern approach: Increase velocity, throughput, capacity, and coverage while reducing cost
To break free from this cycle, IT leaders must make a cultural shift in their perspective. The future of Windows application management doesn’t lie in marginally optimizing old processes, simply changing to new application distribution formats, or putting more and more resources into it—it lies in rethinking the model entirely.
The path forward is clear: automate intelligently.
Tools like Juriba Application Readiness make it possible to dramatically increase throughput, reduce costs, and accelerate update velocity—without sacrificing control or quality.
The traditional method of having control over your Windows applications was to repackage everything that came into your IT environment. During the repackaging process, every app will have its installer rewritten (we refer to this as setup authoring) into a corporate standardized version. This method is resource-intensive and costs a lot of money and time, often involving significant input from the application owner to provide installation instructions, permissions, and expected behaviors. You also have to consider every time to uninstall the old version and newly install the new one.
A more modern approach that we see gaining adoption is to utilize the Windows app vendor-supplied installer, which often has better functionality than can be achieved by rewriting or scripting installers, especially when handling upgrades of older versions. These out-of–the-box installers can be deployed faster using command line installation switches and moving away from authored Microsoft installers. In the modern approach, the package often just needs minor tweaks, i.e., name, install certificate, version, dependencies, etc. These minor changes can be easily scripted using tools like PSADT (PowerShell App Deployment Toolkit).
PSADT can be used as a “script once, use many times” approach. For example, if a new version of Google Chrome is released, using PSADT, you can script all the changes for the update. For all subsequent updates of Google Chrome, the software will recognize the PSADT customizations and apply the scripts automatically.
Of course, this approach will still require smoke testing (or at a bare minimum, managed pilot deployment testing), but this brings us closer to Windows application packaging and testing automation using the vendor-supplied installer to increase velocity, capacity, and throughput of the packaging team.
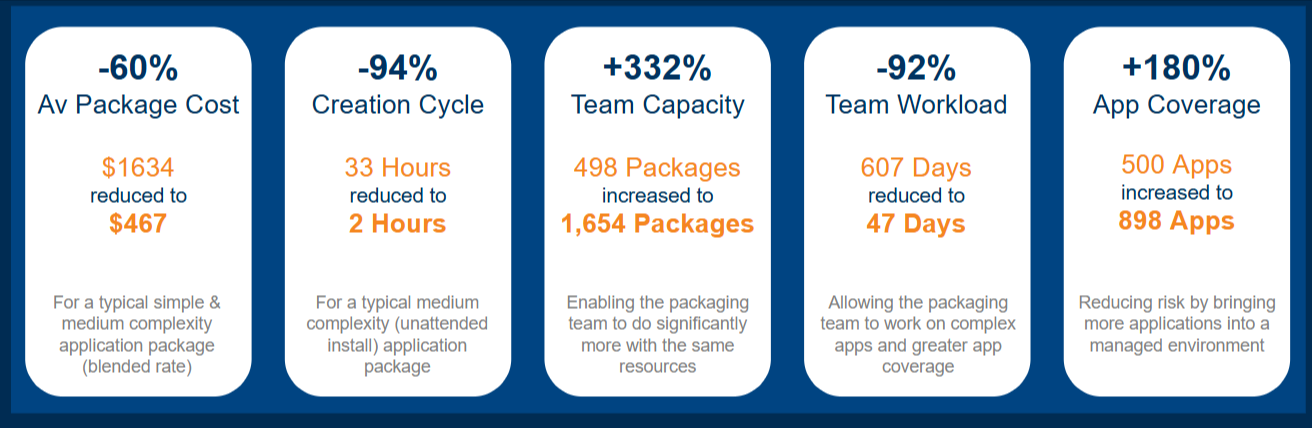
The diagram below shows the type of benefits in a real-world business case that automation can deliver.
Shift-Left: Empowering app owners through self-service and attended repackaging.
Certain Windows applications will always need to be repackaged due to complexities such as applying permissions or setting custom properties, and in many cases, application owners are the ones required to start the process.
The traditional or broken method is:
- Provide the app owner with a clean virtual machine and communicate availability
- They install their Windows application and document it with screenshots and notes, and send it to the packaging team
- The packaging team confirms any further information before running the installation & capturing a snapshot, creating installers, authoring setup scripts, etc., before sending it back to the app owner
- Several rounds of back and forth between the app owner and packaging team typically ensue whilst the application is configured correctly and upgrade scenarios are accounted for
- UAT testing to make sure no mistakes have been made
This method ends up being very time-consuming.

The modern approach is to try and shift the process left through the app owner performing the install themselves and having the flow and customizations captured in a video. They can verify it has worked properly before handing clean outputs over to the Windows application packaging team for review, saving hours of manual effort, reducing the risk of mistakes, and creating a much slicker process.
A scalable future: Confidence, control, and coverage
Then there is a further category of Windows applications that can’t be deployed using the vendor installer and where app owner self-service repackaging won’t work. These applications will need to be repackaged by an expert, but this number is significantly lower than the current volume today. Packaging teams will benefit by having the time to concentrate on these complex applications, giving them the focus they need whilst freeing up time to work on value-added items such as higher Windows application coverage metrics, or velocity and quality initiatives.
By gradually building confidence in automation and shifting more ownership to app teams, organizations can scale their Windows application management sustainably. Over time, app owners may even be empowered to publish and deploy their own applications, using automation tools that enforce governance and compliance in the background.
When combined with complementary efforts like inventory normalization, rationalization, and lifecycle management, this model creates a modern Windows application environment that is secure and efficient.
From reactive to resilient
The traditional approach to Windows application management no longer fits today’s needs and cadence of updates. It’s slow, manual, costly, and increasingly risky. The organizations that will thrive in the years ahead are those willing to challenge convention, embrace automation, and share responsibility across teams.
Windows application management isn’t just an IT task—it’s a strategic enabler of agility and resilience. By modernizing your Windows application packaging workflows, empowering your app owners, and investing in intelligent packaging and testing automation, you’ll reduce risk, lower costs, and unlock the full potential of your application estate. It’s not about doing more of the same. It’s about doing things differently—on purpose.
Barry is a co-founder of Juriba, where he works as CEO to drive the company strategy. He is an experienced End User Services executive that has helped manage thousands of users, computers, applications and mailboxes to their next IT platform. He has saved millions of dollars for internal departments and customers alike through product, project, process and service delivery efficiency.




















.png?width=1600&height=900&name=PSAppDeployKit_FeaturedImage%20(1).png)