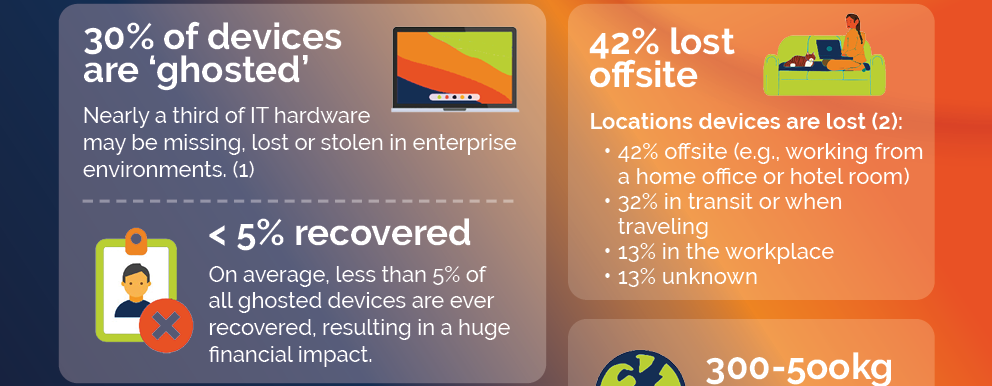
Did you know that, according to an Intel and Ponemon Institute survey, an organization will lose on average 265 laptops per year, but typically only recover 12? In addition to that Gartner estimates that about 30% of enterprise IT hardware may be lost, missing, or "ghosted" in enterprise environments [1].
These seemingly innocuous devices pose a range of risks to enterprises, encompassing financial, security, compliance, and sustainability aspects. This article aims to shed light on the causes and potential impacts of inactive devices, empowering organizations to take proactive measures to mitigate these risks and safeguard their assets.
The cause of ghosted devices
Ghosted devices are a growing problem for businesses. One of the primary causes of ghosted devices is simply losing track of them. A study by Intel and the Ponemon Institute found that 42% of devices are lost offsite, such as in a home office or hotel room, 32% are lost in transit or while traveling, and 13% are lost in the workplace. This problem is often exacerbated by the fact that many organizations do not have a robust asset management system in place, making it difficult to keep track of all of their devices.
Another major contributing factor to the problem of ghosted devices is Shadow IT. Shadow IT refers to the use of IT systems and devices that are not approved or managed by the IT department. Gartner estimates that Shadow IT spending in large enterprises can range from 30% to 40%, while Everest Group puts it closer to 50%. A report by Forbes and IBM found that 60% of organizations do not include shadow IT in their threat assessment, leaving them vulnerable to potential security risks.
Finally, the lack of adequate hardware inventory can also lead to ghosted devices. A study by EY found that 56% of organizations verify their asset locations once a year, while 10-15% of them only track their asset location every five years. Additionally, a Gartner Client Survey revealed that 24% of organizations had not verified their hardware assets in the last five years. This lack of visibility into their hardware assets makes it difficult for organizations to identify and remove ghosted devices.
Financial impact
Lost, missing or ghosted devices can have a significant financial impact on enterprises. The cost of replacing them can be substantial, especially for enterprises with a large number of devices. Many organizations lease their devices, and ghosted devices can incur costs such as $150 per device each year. This can quickly add up to six or seven-figure savings for large organizations.
More importantly, ghosted devices can also lead to lost productivity, data breaches, legal fees, and regulatory fines. For example, if a ghosted device is used to access sensitive data, it could lead to a data breach that could cost the enterprise millions of dollars in legal fees and regulatory fines. Additionally, if it is used to commit fraud, the enterprise could be held liable for the damages.
The financial impact of ghosted devices can be significant, and it is important for enterprises to take steps to mitigate these risks. By understanding the causes of ghosted devices and taking steps to prevent them, enterprises can protect their assets and avoid the financial losses that can result from ghosted devices.
Security impact
The security impact of ghosted devices is a growing concern for enterprises. Unmanaged devices can be targeted for cyber attacks, leaving sensitive data vulnerable to breaches. In addition, devices that are not properly managed can be exploited to gain unauthorized access to your network, potentially leading to a security breach.
Ghosted devices can also be used to bypass security controls, such as firewalls and intrusion detection systems. This can allow attackers to move laterally through your network, gaining access to other systems and data.
Moreover, ghosted devices can be used to launch denial-of-service attacks, which can disrupt your business operations and cause significant financial losses. By understanding the security risks associated with ghosted devices, enterprises can take steps to mitigate these risks and protect their assets.
Compliance impact
Ghosted devices can also have a significant impact on an organization's compliance posture. They can lead to non-compliance with industry regulations and standards, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS).
These regulations and standards require organizations to protect sensitive data and to have adequate security controls in place. Ghosted devices can contain sensitive data that, if not properly disposed of, can lead to data breaches and other security incidents. In addition, ghosted devices can complicate software license compliance, as enterprises may be paying for licenses for devices that are no longer in use or accessible.
Sustainability impact
The impact of ghosted devices on the environment cannot be overstated. E-waste, or electronic waste, is a term used to describe discarded electrical or electronic devices. It is one of the fastest-growing waste streams globally, and ghosted devices certainly contribute to this problem.
The manufacturing of new devices also has a significant carbon footprint. The extraction and processing of raw materials, the assembly of the devices, and the transportation of the finished products all contribute to greenhouse gas emissions. By extending the lifespan of devices and reducing the need for new production, organizations can help to reduce their environmental impact.
In addition to the environmental impact, ghosted devices can also have a negative impact on an organization's sustainability efforts. For example, if an organization is trying to reduce its energy consumption, ghosted devices can continue to draw power even when they are not in use. This can lead to increased energy costs and a larger carbon footprint.
Organizations should take steps to mitigate the sustainability impact of ghosted devices by implementing asset management programs, regularly auditing their devices, and properly disposing of ghosted devices. By taking these steps, organizations can help to reduce e-waste, lower their carbon footprint, and improve their overall sustainability performance.
Conclusion
In conclusion, organizations should implement a robust device management program to minimize financial losses, enhance security measures, reduce compliance risks associated with lost, missing or 'ghosted' devices and protect their sensitive data. In addition, they should regularly audit their devices, encrypt sensitive data, implement strong security controls, and educate employees about proper device disposal.
To assess the risk your organization is facing from ghosted devices, complete our free assessment. It consists of 16 questions and takes less than five minutes, but you will not only get a clear idea of what your risk level is but also what questions you need to ask yourself to dig deeper into any potential inactive device issues you might have.
(1) Gartner, 1 Gartner, Complete Guide to a Sustainable Device Life Cycle Using the IT Circular Economy
(2) Intel and the Ponemon Institute Survey, The Billion Euro Lost Laptop Problem, https://www.intel.ie/content/dam/doc/case-study/mobile-computing-security-eu-benchmark-study.pdf
Gartner about Shadow IT: https://www.cio.com/article/234745/how-to-eliminate-enterprise-shadow-it.html
IBM/Forbes (original PDF was just deleted so I changed the link): https://ramp.com/blog/what-is-shadow-it
Everest Group about Shadow IT: https://www.everestgrp.com/in-the-news/dont-fear-shadow-it-embrace-it-in-the-news.html
(3) EY Study (original PDF no longer available): https://www.ivanti.com/blog/itam-and-endpoint-security-you-can-t-manage-secure-and-effectively-defend-against-what-you-don-t
(4) UN University Global E-Waste Monitor mentioned in the Gartner report (1)
(5) EMC: https://www.securityweek.com/downtime-and-data-loss-cost-enterprises-17-trillion-year-emc/
$6.4 million https://www.intel.ie/content/dam/doc/case-study/mobile-computing-security-eu-benchmark-study.pdf
Interactive quiz: What's your risk? Find out!
Is your organization at risk of security vulnerabilities, productivity losses and costs caused by a high number of inactive or ghosted devices? Answer 16 questions to find out.
Take the quiz now
[1] Gartner, The Complete Guide to a Sustainable Device Life Cycle Using the IT Circular Economy, Autumn Stanish, Annette Zimmermann, September 7, 2022
Like this blog? Try these:
Benefits & challenges of device reclamation to prevent ghosted devices
Read the blog
16 questions you need to ask to assess the risk of lost or missing devices
Read the blog
Barry is a co-founder of Juriba, where he works as CEO to drive the company strategy. He is an experienced End User Services executive that has helped manage thousands of users, computers, applications and mailboxes to their next IT platform. He has saved millions of dollars for internal departments and customers alike through product, project, process and service delivery efficiency.
Topics:












