What are inactive or 'ghosted' devices and why should you care?
January 25th, 2024
6 min read
By Barry Angell

With up to 76% of all full-time workers being knowledge workers, organizations rely heavily on employee devices such as laptops, PCs, and mobile phones to conduct business and store sensitive data. However, managing these devices can be a major problem, especially when they become misplaced, lost, stolen, or abandoned. These devices, known as inactive or ghosted devices, can be costly and complex to mange and reclaim, and can pose a significant security risk to large organizations.
Many large organizations currently try to manage this process manually across thousands of devices, with spreadsheets, endless emails, follow ups, and chasing line managers, all leading to up to 30% of devices remaining dark or missing. Here at Juriba, we help large organizations and enterprises to accurately and efficiently automate the management of their device inventories and lifecycles.
Over the next weeks, we will go deeper into the impact of ghost devices and explore ways you can reclaim and proactively manage your devices to prevent device ghosting. In this article, the first in this mini-series, we will discuss the causes and impact of ghosted devices. By understanding and addressing the issue of ghosted devices, you can enhance their security posture, optimize your IT asset management practices, and save up to 30% on leasing and license fees.
What is a ghosted device?
With regards to IT asset management, a ghosted device, also referred to as inactive devices, can be defined as follows:
A ghosted device refers to a computer, laptop, or mobile device that is misplaced, lost, stolen, intentionally abandoned by its user, or rendered unusable, yet remains listed as an active fixed asset in an organization's system.
These devices pose significant security risks as they may contain sensitive data that could be accessed by unauthorized individuals, potentially leading to data breaches and other security incidents.
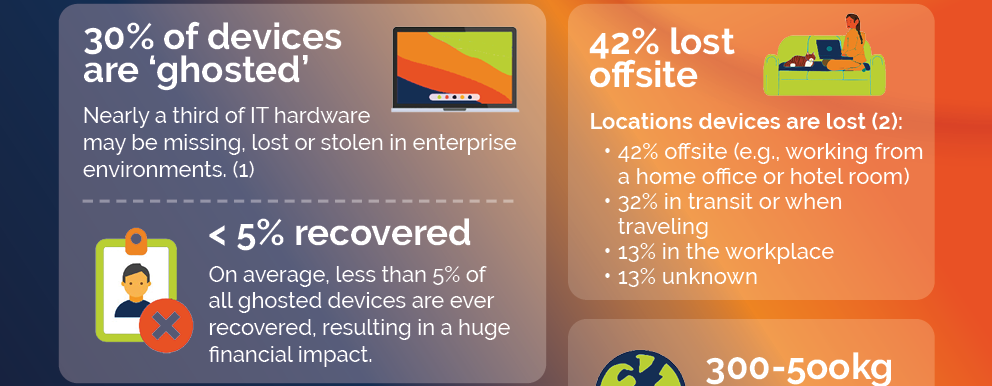
The prevalence of ghosted devices is a pressing concern for organizations of all sizes. According to Gartner, a staggering 30% of hardware assets are reported to be stolen, missing, lost or, in other words, "ghosted." This alarming statistic underscores the importance of addressing this issue proactively to safeguard sensitive information and maintain overall cybersecurity.
About 30% of enterprise IT hardware may be lost, missing or "ghosted" in enterprise environments today, which happens at any stage of the lifecycle - from procurement to provisioning to upgrading.
Gartner: The Complete Guide to a Sustainable Device Lifecycle Using the IT Circular Economy
Ghosted devices can enter an organization's system through various means. Some common scenarios include employee negligence, such as leaving devices unattended in public places or failing to report lost or stolen devices promptly. Intentional abandonment of devices can also occur when employees leave the organization without properly decommissioning their devices. Additionally, devices may become unusable due to hardware failures or software malfunctions but remain listed as active assets due to poor asset tracking practices.
Impact of ghosted/inactive devices on large organizations
The impact that ghosted devices can have on your organization is huge, affecting various aspects of your operations and potentially leading to substantial costs and security breaches.
Financial and Operational Impact: Ghosted devices pose a significant financial and operational burden on large organizations. The hidden costs of replacing lost or stolen IT hardware, ongoing expenses for unused leasing contracts and software licenses, and the resources required to investigate and resolve security incidents are substantial. These costs can heavily strain an organization's budget, diverting funds from essential business areas. Additionally, the mismanagement of fixed assets like IT equipment, a major investment for most companies, often results in overlooked opportunities for savings and operational efficiency.
Security Risks: The presence of ghosted devices in an organization's network significantly elevates security risks. These devices, often loaded with sensitive data, are prime targets for data breaches and identity theft if acquired by unauthorized parties. Such security incidents can lead to severe financial and reputational damage. For instance, Gartner once discovered that a client had 60% more devices connected to their network than documented, raising concerns about potential unauthorized access and the origin of these unregistered devices.
Productivity, Efficiency, and Sustainability Effects: Ghosted devices also negatively impact employee productivity and efficiency, disrupting workflows and the organization's ability to meet its objectives. Additionally, the improper disposal or recycling of these devices contributes to electronic waste, counteracting the organization's sustainability efforts. To counter these risks, it's crucial for organizations to implement robust management and tracking systems for IT devices, conduct regular audits, and educate employees about responsible device usage. Proactive steps like these not only protect sensitive data but also promote operational efficiency and align the organization with sustainable practices.
What are common causes for inactive or ghosted devices?
Given the fact that one in three devices you are currently paying for isn't accessible or usable, you might be asking yourself: "How can this happen?" Let's have a closer look at the most common causes of ghosted devices.
Ghosted devices may start with organizational structure and culture
Nobody owns the process. In most organizations, nobody is responsible for keeping track of hardware devices. Usually, a large number of inactive devices is discovered as part of larger projects, like a Windows 11 upgrade or a Digital Workplace initiative.
Shadow IT. Shadow IT occurs when employees use devices or software without the knowledge or approval of the IT department. This is very common in larger organizations. These devices may not be properly secured or managed, increasing the risk of being ghosted. Also, since IT doesn't know about them, the employee might "forget" to return the device after their contract has been terminated or after they quit.
Insufficient security measures and processes. Insufficient security measures and processes can make it easier for unauthorized individuals to access sensitive data on ghosted devices. Organizations need to have strong security measures in place to protect their data, such as encryption, access controls, and firewalls.
Employee negligence or lack of training. Employee negligence or lack of training can also lead to ghosted devices. Employees need to be properly trained on the importance of device security and the consequences of losing or abandoning devices.
Lack of visibility into cost of ownership. Finally, lack of visibility into cost of ownership can make it difficult for organizations to justify the expense of replacing ghosted devices. Organizations need to have a clear understanding of the cost of ownership for their devices, so they can make informed decisions about when to replace them. For example, old devices are often just put into storage closets (just in case we hire that intern) rather than handed back to IT. If the manager knew that it is costing the company (and their department) $150 a month for a leasing contract, they would probably ensure that the device was recovered and the proper procedure was followed.
The buck stops with adequate device management & compliance
When everything is said and done, it comes down to two things: you need the proper tools to proactively and efficiently manage your devices, and you need processes in place to prevent ghosted devices from happening.
Insufficient tracking and monitoring of asset locations
You cannot manage your devices if you don't know how many you have and where they are. A recent survey revealed that 56% of organizations will only verify the location of their devices once a year, while 10 to 15% admit that they only track them every five years!
The challenge has increased with remote working and a reduced office presence. People used to drop off devices at the office or service bars, or give them to IT. Now, however, insufficient tracking and monitoring of asset locations is one of the biggest contributors to the prevalence of ghosted devices. Organizations need to have systems in place to track the location of their assets so they can be quickly located if they go missing.
Lack of device management and tracking systems/tooling
One of the main reasons that organizations so rarely track their assets' locations is because they simply lack the tools. Most organizations with ghosted devices don't have adequate device management and tracking systems in place to keep tabs on their assets. Instead, they use instantly out-of-date spreadsheets, purchase orders, or simple network discovery tools.
Consequently, tracking hardware with these antiquated methods is an administrative nightmare as IT assets are constantly assigned, reassigned, and moved around from one department or location to another. It is no wonder that devices are being misplaced, lost, or stolen without the organization's knowledge.
Lack of automated, standardized, and repeatable processes
However, tooling alone won't solve the problem. You need automated, standardized, and repeatable processes that go with that. For example, what happens when an employee leaves the company? Or a laptop gets stolen? Or it's inactive for more than 30 days on your network? Would you know about it? How would each of those scenarios be handled? Without those processes and procedures in place (including ways to enforce them), your attempts to minimize your ghosted devices will only go so far.
Conclusion
Ghosted devices pose significant security risks and have a negative impact on large organizations. With up to 30% of hardware assets reported to be ghosted, it is crucial for organizations to address this issue proactively.
By implementing robust device management and tracking systems, conducting regular audits, and educating employees about responsible device usage, organizations can enhance their security posture, optimize IT asset management practices, and save on leasing and license fees.
In the next articles of this mini-series, we will dive deeper into the impact of ghosted devices on large organizations and explore ways to prevent and combat device ghosting. Stay tuned for more insights and practical solutions to effectively manage your devices and protect your sensitive data.
Calculate the cost of inactive devices in your organization
Inactive devices are the elephant in the room conversation. But if you could see the financial impact, would you keep ignoring it?
Try the cost calculatorLike this blog? Try these:
The impact of ghosted devices on enterprises
Read the blog
16 questions you need to ask to assess the risk of lost or missing devices
Read the blog
Barry is a co-founder of Juriba, where he works as CEO to drive the company strategy. He is an experienced End User Services executive that has helped manage thousands of users, computers, applications and mailboxes to their next IT platform. He has saved millions of dollars for internal departments and customers alike through product, project, process and service delivery efficiency.
Topics: