16 questions you need to ask to assess the risk of lost or missing devices
February 12th, 2024
5 min read
By John Garner

Between laptops, tablets, phones, & peripheral devices, large organizations can easily have tens if not hundreds of thousands of devices to keep track of at any given time. Despite the myriad of tools to help manage IT assets, many organizations still struggle to piece together siloed sets of data from purchase orders, departmental records, HR reports, etc. for the up to date location and status of these devices. With every lost, missing, or inactive device impacting the bottom line, the financial leakage impact for organizations can be significant.
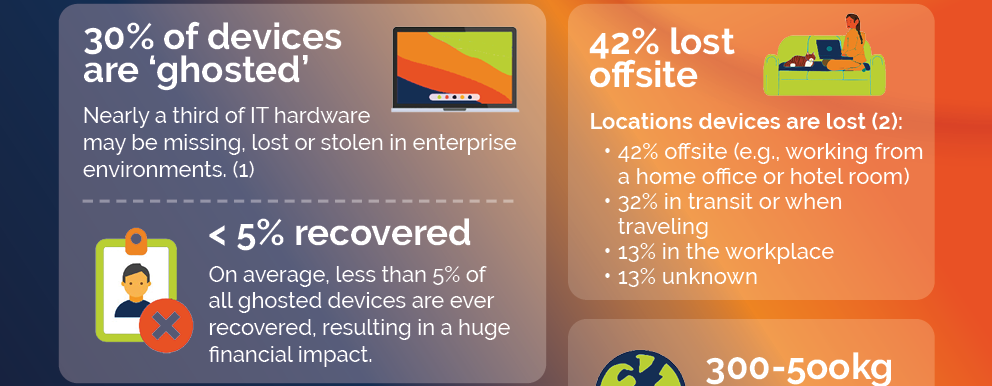
Lost, missing, or stolen devices are often referred to as 'inactive' or 'ghosted'. We have helped hundreds of large enterprises, financial institutions, and government agencies create an accurate and up-to-date hardware inventory, implement device lifecycle management programs, and automate device reclamation initiatives through which they recovered ghosted or inactive devices that accounted for as much as 30% of their total device count.
In this article, I will share the 16 questions every Digital Workplace leader, IT leader, or CIO/CTO should ask themselves to assess their organization's risk of lost, missing or inactive devices and the security vulnerabilities, productivity losses, and costs that are associated with them.
Take the ghosted device risk assessment quiz today!
Lost or missing devices put you at great risk
The impact that ghosted devices can have on your organization is huge, affecting various aspects of your operations and potentially leading to substantial costs and security breaches.
Lost or missing devices are costing you — a lot!
Most organizations struggle with managing their fixed assets. Fixed assets, like end user devices, are some of the biggest investments and can have the largest sustainability impact for enterprise organizations, yet the savings potential achieved by managing them correctly is often overlooked.
Specifically for ghosted devices, the financial implications are multifaceted. Organizations may incur costs related to:
- Resourcing to track and manage devices effectively,
- The cost to replace lost or stolen devices,
- Paying leasing contracts (and potential end of term penalties)
- Unused software licenses,
- Investigating and resolving security incidents,
- And much more.
These expenses can strain an organization's budget and divert resources from other critical areas.

Device ghosting significantly increases your security risk
Ghosted devices present heightened security risks. These devices often contain sensitive data, making them attractive targets for unauthorized individuals. If these devices fall into the wrong hands, the result can be data breaches, identity theft, and other security incidents. The financial and reputational consequences of such incidents can be severe, potentially damaging an organization's credibility and bottom line.
Inactive devices impact your productivity, efficiency, and sustainability
In addition, ghosted devices effect your employees' productivity and efficiency. When employees lack access to the devices necessary for their tasks, it disrupts workflows and hampers productivity. This directly affects the organization's ability to achieve its goals and can lead to missed deadlines and subpar performance. They can also negatively impact your organization's sustainability efforts as improper disposal or recycling of these devices contributes to electronic waste and environmental pollution. This not only harms the organization's reputation but also undermines its commitment to sustainable practices.
To mitigate the risks associated with ghosted devices, large organizations must take proactive steps. Implementing robust device management and tracking systems, conducting regular audits to identify and address ghosted devices, and educating employees about responsible device usage are essential measures. By addressing this issue effectively, organizations can safeguard their operations, protect sensitive data, optimize productivity, and align with sustainable practices.
To help minimize these risks, use the questions below to first assess your risk and then start putting strategies in place for mitigating these risks. We grouped the questions in three logical buckets: inventory management, asset management processes, and lost-device management.
Inventory management questions you need to ask
A few weeks ago, we defined a ghosted device as a computer, laptop, or mobile device that is misplaced, lost, stolen, intentionally abandoned by its user, or rendered unusable, yet remains listed as an active fixed asset in an organization's system. So, the obvious way to start assessing your risk for misplaced, lost, stolen or otherwise vanished devices is to take a closer look at your inventory management.
Inventory management is a critical aspect of managing the risks associated with ghosted devices, such as asset mismanagement, huge leasing, software, and other costs tied to the device, serious security vulnerabilities, and loss of productivity. Effective inventory management processes help identify these ghosted devices early, ensure accurate asset tracking, and maintain the integrity of your organization's technology assets. These five questions will give you more clarity regarding the effectiveness of your device inventory management:
- Do you utilize any tracking or management software to monitor the location and status of your IT devices?
- How accurate is your device inventory?
- Do you have a process for identifying and reconciling discrepancies in your device inventory?
- How frequently do you conduct physical audits of IT devices against your inventory records?
- Is there a process for identifying and retiring underused or outdated devices?
Now that you know how accurate your hardware inventory is, let's have a look at the next piece of the puzzle: your lost device management processes.
Lost device management questions you need to ask
Until now, we have talked mostly about how you can prevent ghosted devices. However, it is equally important to discuss how you manage lost devices. Understanding your lost-device rate, knowing how much time and money you spent on lost devices at any given time, and being aware of how fast and successful you are in recovering ghosted machines gives you a good indication of where you stand.
- Do employees receive training on the importance of device security and the procedures for reporting lost or stolen devices?
- Do you have a process for reporting and tracking lost devices?
- How well do you understand and track the cost impact of lost devices?
- How much time is spent managing lost devices each week?
- What is your organization’s lost-device rate?
- What is your organization’s success rate in recovering lost devices?
- How quickly does your organization replace lost or damaged devices?
Asset management processes questions you need to ask
An up-to-date inventory and efficient lost-device management is only going to get you so far if you don't have the right processes in place to manage your assets. It would be like trying to clean your desk with the fan blowing on it.
To keep your hardware inventory accurate, you need to create standardized processes from the moment you procure a device, through the time it is issued to a user, and all the way to the moment when it is decommissioned and disposed of or recycled. In addition, in order to minimize any security exposure, you will need processes to manage replacements and manage what happens if a device gets lost.
The four questions below will help you assess your asset management processes:
- Is there a formal process for issuing devices to employees, including documentation and acknowledgment?
- Are there robust security measures in place for devices that are reported lost or stolen?
- Is your replacement process efficient and cost-effective?
- Do you have a formal process for the environmentally responsible and safe disposal or recycling of devices that are no longer in use?
Conclusion
In conclusion, the risks associated with ghosted devices in organizations are significant and can have a detrimental impact on operations, security, productivity, and sustainability. The financial implications of ghosted devices, including costs for replacement, leasing contracts, software licenses, and security incidents, can strain an organization's budget and divert resources from critical areas. Moreover, ghosted devices raise security risks as they often contain sensitive data, making them attractive targets for unauthorized individuals. Inactive devices also hinder productivity, efficiency, and sustainability efforts.
To assess the risk of ghosted devices, organizations should investigate three main areas: inventory management, asset management processes, and lost-device management. By taking just five minutes to complete the risk assessment, organizations can gain insight into their risk level and take proactive steps to mitigate these risks. Don't wait! Take the assessment today and safeguard your organization's operations, protect sensitive data, optimize productivity, and align with sustainable practices.
Like this blog? Try these
Benefits & challenges of device reclamation: recovering lost or missing devices
Read the blog
The impact of ghosted devices on enterprises
Read the blog
An independent HP DDMi Consultant with over 15 years IT experience in FMCG, Telecoms, Health and banking environments. A logical thinker with excellent interpersonal skills and an extensive knowledge of Asset management, network protocols, business systems, Configuration and analytical toolsets. With a broad understanding of project management and outstanding technical capabilities in HP DDMi I can undertake any implementation from conception to completion.
Topics: